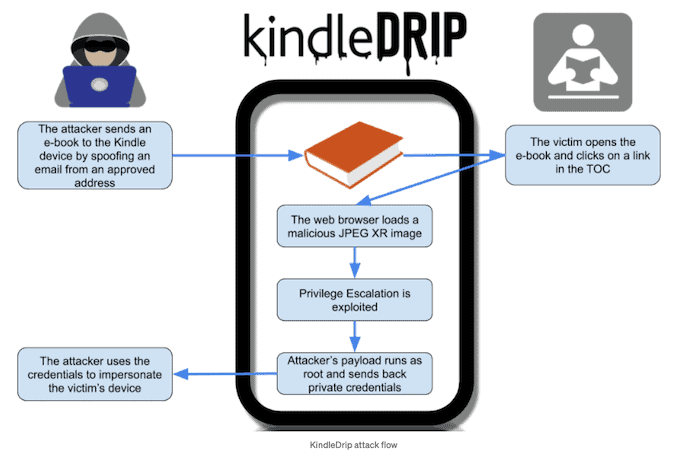
Bar-On noticed that in order to submit a specially designed e-book that would allow him to execute arbitrary code on the targeted computer, he could exploit this function. By exploiting a flaw relating to a library used by the Kindle to parse JPEG XR files, the malicious e-book achieved code execution. Exploitation allowed the user to click on a connection that included a malicious JPEG XR image within an e-book, which would open a web browser and run the attacker’s code with restricted privileges. The researcher also found a loophole that allowed him to increase privileges and run the root code, allowing him full access to the system.
The intruder was able to obtain computer passwords and make transactions using the victim’s credit card at the Kindle store. In a blog post, Bar-On clarified that attackers could sell an e-book at the store and pass cash to their account. The confirmation email will at least make the victim aware of the transaction.’ An attacker will only require the email address of the intended user and to induce the victim to click on a connection inside the malicious e-book. While the Send to Kindle function only encourages users to send e-books from pre-approved email addresses, the investigator found out that an intruder may simply have used an email spoofing service. In certain instances, the intended user’s @kindle.com email address prefix is the same as their daily email. To explain how a KindleDrip attack worked, a video was published: