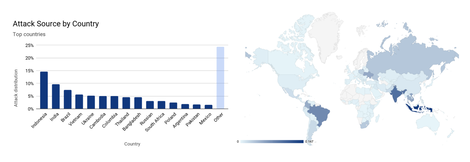
Cloudflare claimed that its system was able to stop the largest DDoS attack reported in July. They explained in a blog post how the attack was 17.2 Million requests-per-second, which is three times more than any other one they have recorded. Cloudflare’s Omer Yoachimik explained in a blog post that the company serves over 25 million HTTP requests per second on average in 2021 Q2, illustrating the enormity of the attack. He said that the botnet was attacking a customer in the financial sector of Cloudflare. He said that it was able to reach Cloudflare’s edge with more than 330 million requests in less than a second. Yoachimik pointed out that two weeks prior, a Mirai variant botnet had launched over a dozen UDP- and TCP-based DDoS attacks. These attacks peaked multiple times at 1 Tbps with a maximum peak of about 1.2 Tbps. “This 17.2 million rps attack is the largest HTTP DDoS attack that Cloudflare has ever seen to date and almost three times the size of any other reported HTTP DDoS attack. This specific botnet, however, has been seen at least twice over the past few weeks. Just last week it also targeted a different Cloudflare customer, a hosting provider, with an HTTP DDoS attack that peaked just below 8 million rps.” Customers of Cloudflare, including a gaming company as well as a major APAC-based telecommunications provider and hosting provider, are being attacked with attacks on the Magic Transit and Spectrum services along with the WAF/CDN service. Yoachimik claims that the Mirai botnet generated significant attack traffic, despite being smaller than its original 30,000 bots. “Additionally, based on the current August per-day average of the Mirai attacks, we can expect L7 Mirai DDoS attacks and other similar botnet attacks to increase by 185% and L3/4 attacks by 71% by the end of the month.” He pointed out that botnets like Mirai, which launched the attack on Mirai, heavily depend on compromised IoT devices as well as other unmanaged devices. “As the number of these devices grows, so too does the potential army for DDoS attacks,” Ting said. Yoachimik stated that their autonomous edge DDoS protection systems detected the 17.2million attack. He also noted that their system is powered a software-defined, denial of service damon they call dosd.