When spam campaigns are conducted, the actors behind Emotet use malicious Word document templates to trick the recipient into the document’s macro. Upon enabling these macros the script will download and install the Emotet Trojan and potentially other malware on the desktop of the recipient. While spam messages still use a combination of answer-chain and direct e-mails which claim to be false invoices, order confirmation, payment confirmations and shipping problems, they have now changed to a fresh document template, which claims to be an activation wizard in Microsoft Office.
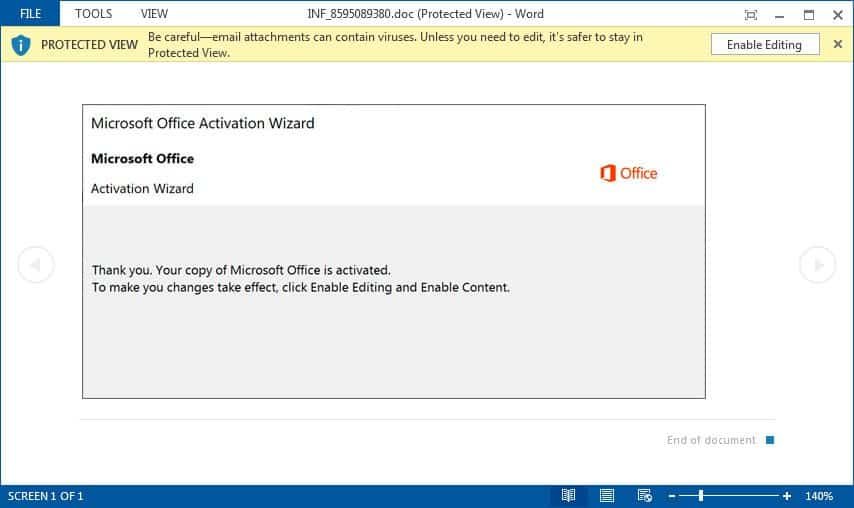
Example of an Emotet reply-chain email This fresh model discovered by the safety investigator ps66uk enables the victim to click on the Enable Content buttons to finish Microsoft Office activation.
Microsoft Office Activation Wizard template Ps66uk informed that the investigator saw this specific document template used by Emotet for the first moment. Once the user presses the Enable Content Edit and Enable buttons, built-in macros will launch a PowerShell command connecting to a distant site, download the Emotet Trojan to the percent UserProfile percentage of the victim and perform this. Once infected, the Trojan Emotet will send additional spam mails to the contact lists of the victim and download other malware to your desktop.
Protect yourself against malicious attachments
If the Emotet botnet sends spam emails, it appears from senders you know about and is sometimes used to answer the current messages in which you have been engaged. It is therefore reasonable for a recipient to believe that an e-mail is valid and so that the attachment is opened. Unfortunately, as mentioned above, repeat-chain attacks make it hard to trust any attachments you obtain. Because of this, I recommend that you call the sender directly to verify that they sent an attachment via email. You shouldn’t open it otherwise.