Online services for hackers are what we thought were–scams and ineffectiveness–new research published by Google last week and researchers from the University of California, San Diego, has been disclosed. “We have engaged directly with 27 such account hacking service providers with unique online purchasers and asked them to compromise our victim account,” said researchers. “Their victims, on the other hand, were’ honey-pot ‘ Gmail accounts, operated in coordination with Google, enabling us to record key interactions with both the victim and other manufactured aspects of their online person that we created (for example business web servers, friendly or partner email addresses). Of the 12 responding but never attacking, nine said that they hacked Gmail accounts anymore, while the other three seemed to be scams.
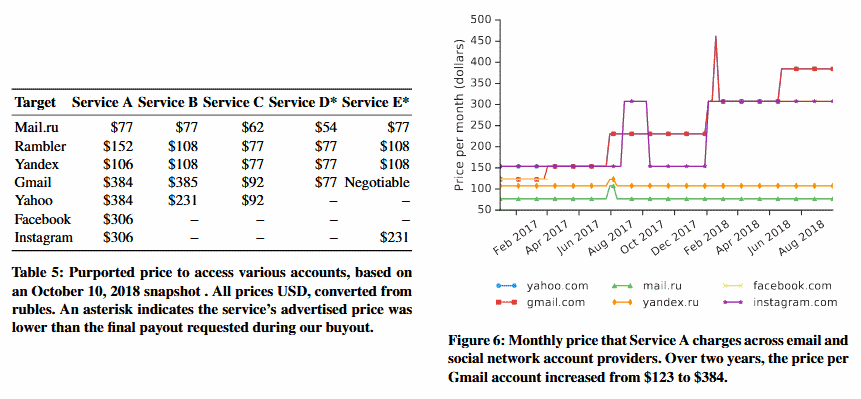
Image: Mirian et al. Researchers said services generally charge their services between $100 and $500, and none of them used automated attack tools. Every attack involved social engineering, and every victim was subjected to spear-phishing hackers. Some hackers asked about the victim they were supposed to target while others did not bother and chose to use reusable templates. The strangest thing about the five hackers who launched an attack is that one of them attempted a malware infection (a Trojan remote access) rather than the victim’s account credentials. Once the malware had been installed in the victim’s system, it could retrieve local browsers ‘ passwords and authentication cookies. In addition, one attacker could circumvent two-factor authentication (2FA) by redirecting the victim to the spotted Google connector page that collected both passwords and SMS codes and checked the validity of both in real time. In addition, the research team found that hackers who learned that 2FA must be bypassed usually double their prices. Researchers also observed that Gmail’s hacking prices increased over the years from $125 per account in 2017 to approximately $400 today. The price rise was attributed to Google’s improvement of account security measures.
Image: Mirian et al. In general, we find the marketed account hijacking ecosystem far from mature, “said the research team.” We have frequently encountered poor customer service, slow response and inaccurate pricing advertisements. “In addition, the current 2FA bypassing techniques may be mitigated through the adoption of U2F security keys,” they added. Researchers ignored scam sites and claimed they did not consider hacker-for-hire services as a risk to user accounts. It is because of the high prices for each account hacking, but also because of their low quality of service. Further details on the research are available in a White Paper entitled “Hack for Hire: Exploring the Emerging Market for Account Hijacking.” Last week Google also published a further study showing that adding a Google recovery telephone number significantly reduces automated hijack attempts efficiency.