Businesses use SEGs to safeguard themselves from a broad range of email assaults. They scan for malicious material in and out of every message and at least safeguard against malware and phishing threats.
Captcha automatic scanning blocks
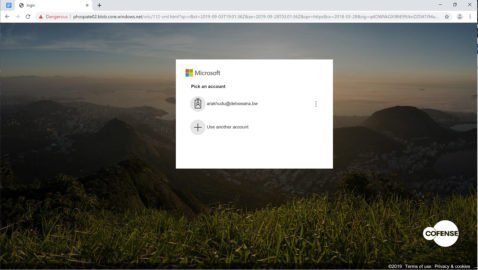
Captchas are challenging techniques for determining whether the user is human or bot. It is intended to avoid violence and is normally discovered on registration websites to avoid automated registration. Ironically, Cofense’s phishing campaign used this sort of task to prevent automated URL assessment from processing a hazardous page. “The SEG cannot proceed to and scan the malicious page, only the Captcha code site. This webpage doesn’t contain any malicious items, thus leading the SEG to mark it as safe and allow the user through.” – Cofense After admission to Microsoft accounts, the attackers developed a page imitating the original for account selection and login.
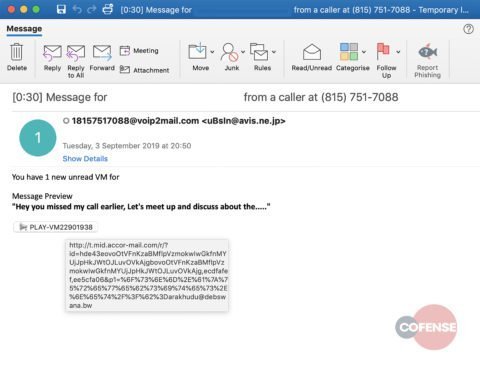
This is served after the human verification phase has been completed. It goes without saying that everything typed in text fields is sent to the attacker automatically. According to the scientists, the phishing link delivered by email from a compromised’ avis.ne.jp’ account pretends to be a voicemail notification. A button which promises to give an overview of the supposed interaction is integrated in the email; it brings the victim to the captcha code page when clicking.
The scientists claim that both the captcha and phishing pages of the Microsoft infrastructure are hosted. They have lawful top-level domains, which guarantees that the domain reputation databases used by SEGs do not react negatively in their URL assessment. Creative cyber criminals are always looking for fresh ways to circumvent security controls and displaying social engineering tricks in trying to pass human inspection. Fraudsters used QR codes in recent campaigns to redirect their data to phishing sites, a technique that also falls under the various safety solutions radar. Another transaction depended on email notifications of a file shared by the target Google Docs. When users attempted to open the file, a false 404 error would be found and the file would be downloaded locally. Threat performers used false 2FA codes supplied via messages pretending to be from Instagram to make another email scam more credible. Credit:Bleepingcomputer