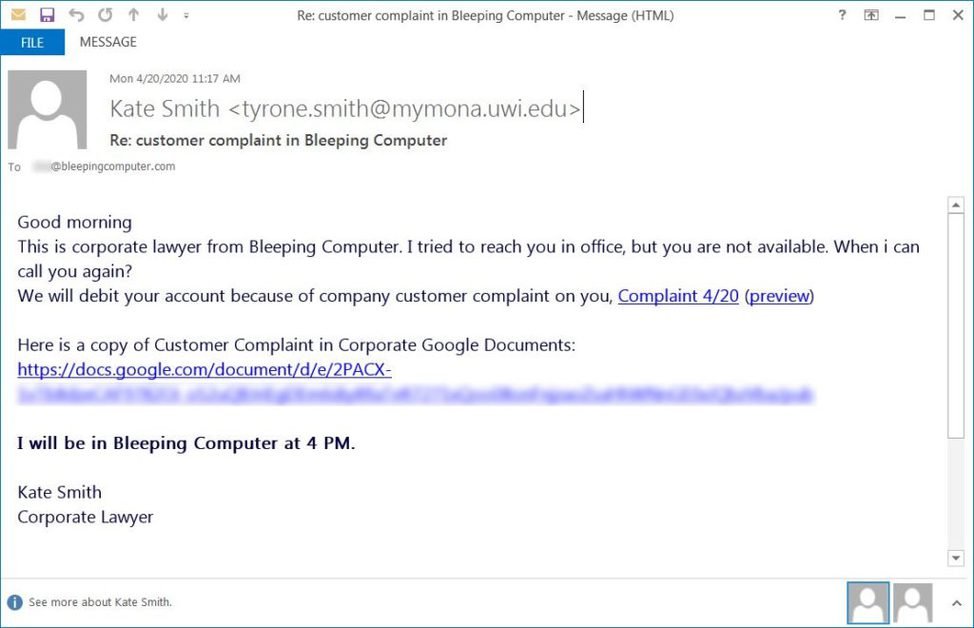
There is a recent phishing campaign targeted at workers in business with false customer grievances that create a new backdoor to jeopardize a network. For the past two weeks, BleepingComputer and others we’ve been talking to receive malicious emails from “corporate lawyers” of their business. Subjects such as “Re: customer complaint in [insert company name]” or “Re: customer complaint [recipient name]” are included in such letters, which indicate that a consumer allegation has been submitted to the recipient’s employer. As a result, the employee is disciplined, and his pay is deducted. Clicking on the “Expand and Display” link will open a file called Preview.PDF.exe. This phishing mail specifically targets corporate networks. Many researchers have seen a new backdoor spread through phishing emails in recent weeks containing a link to a fake PDF of Google Docs. As mentioned above, a user who attempts to access the PDF on Google Docs is prompted to “Expand and Preview,” so that it can download a file. The file name is Preview. PDF.exe in our phishing attack and is signed by the certificate of “VB Corporate PTY, LTD.” When executed, the malware will insert itself into the C:\Windows\system32\svchost.exe legitimate server and then connect to a remote server to send data and receive additional commands or payloads. According to James security researchers, this backdoor was called the “bazaloader” for command and control servers, which uses the Blockchain-DNS solver and associated “Bazar” domain. BleepingComputer was told in discussion with James that the cobalt attack was installed on compromised networks. If the Cobalt attack is activated, attackers will have complete access to the victim’s device. They will use it to jeopardize the entire network and install malware or steal data for extortion.